Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
33 Kubernetes security tools
Kubernetes security tools … there are so freaking many of them; with different purposes, scopes and licenses. That’s why we decided to create this Kubernetes security tools list, including open source projects and commercial platforms from different vendors, to help you choose the ones that look more interesting to you and guide you in the right direction depending on your Kubernetes security needs.
How to detect Kubernetes vulnerability CVE-2019-11246 using Falco
A recent CNCF-sponsored Kubernetes security audit uncovered CVE-2019-11246, a high-severity vulnerability affecting the command-line kubectl tool. If exploited, it could lead to a directory traversal, allowing a malicious container to replace or create files on a user’s workstation. This vulnerability stemmed from an incomplete fix of a previously disclosed vulnerability (CVE-2019-1002101). Are you vulnerable?
Investigate and Correct CVEs with the K8s API
When NIST (https://nvd.nist.go) announces a new CVE (Common Vulnerability and Exposure) that impacts Kubernetes, kube administrators and IT Security teams need to quickly understand the impact of the vulnerability and protect their Kubernetes clusters. Often, no patches are yet available, so in addition to understanding the impact, DevOps teams have to decide whether or not to create a custom fix to mitigate the risk of that CVE without bringing down the entire app or system.
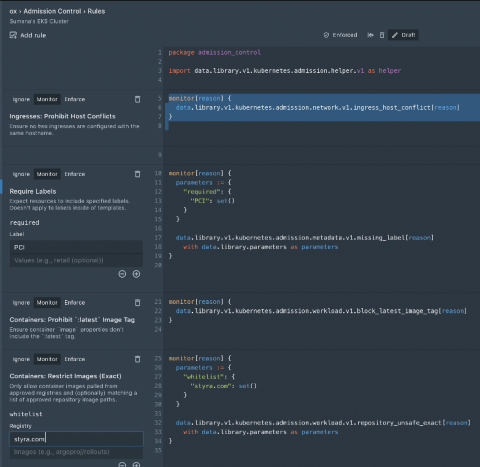
How to implement guardrails for AWS EKS
Today marked the first ever AWS re:Inforce security conference, and Styra was well represented. Paavan Mistry from AWS took the stage to walk through an EKS Security session with Synamedia, wherein they talked about the great responsibility organizations have over their Kubernetes environments.
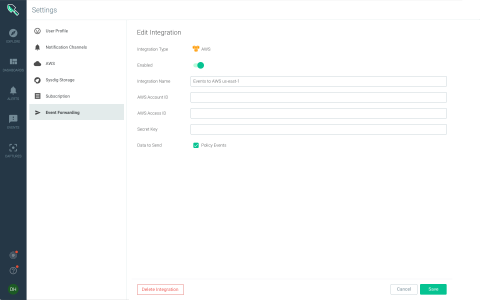
Sysdig Secure now integrates with AWS Security Hub
Today, Sysdig is proud to announce our integration with the AWS Security Hub. AWS Security Hub consolidates alerts and findings from multiple AWS services including, Amazon GuardDuty, Amazon Inspector, as well as from AWS Partner Network (APN) security solutions, which Sysdig is already a part of. This single pane of glass gives you a comprehensive view of high-priority security alerts and compliance status across AWS accounts.
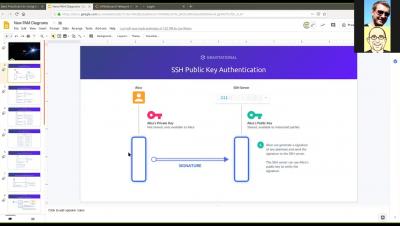
Single Sign-On for Kubernetes: The Command Line Experience
One of these problems is that Kubernetes has no login process. Ordinarily, the client software would initiate this login flow, but kubectl does not have this built in. Kubernetes leaves it up to you to design the login experience. In this post, I will explain the journey we took to get engineers logged in from the terminal and the challenges we faced along the way. The first step to SSO was to set up Dex as our Identity Provider.
KlusterKit - Enable Kubernetes based Architectures in Air Gapped Deployments
Early adopter enterprises across verticals such as Retail, Manufacturing, Oil & Gas are looking to incorporate containers and Kubernetes as a way of modernizing their applications. Choosing k8s as a standard ensures that these applications can be deployed these on different data center infrastructures (bare metal/VMware/KVM on OpenStack etc) or on public clouds (AWS/Azure/GCP etc).
Containerized Air Gapped Edge Platform Architecture
An emerging use case for containerized platforms has been the ability to deploy applications in what is termed as an air-gapped deployment. This deployment pattern is particularly pronounced around edge computing (more on that later in the blog series) – though there exist significant differences between edge clusters and air-gapped deployments. Air-gapped applications are those that run isolated from datacenter or internet connectivity.
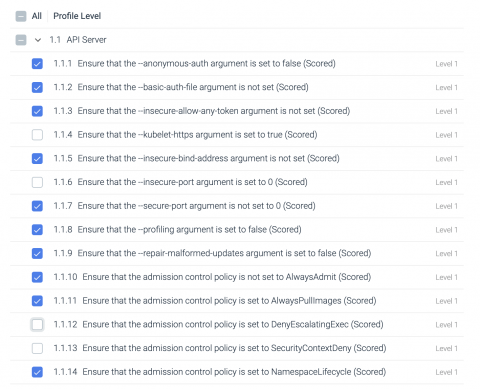
Custom compliance filters with Sysdig Secure
Custom compliance filters is now GA as part of the SaaS and on-prem release. With Sysdig Secure, enterprises can enforce compliance filters across the container lifecycle. Teams can automate regulatory compliance controls for PCI, NIST, CIS, for Kubernetes and container environments at scale.They also gain visibility into the performance, health, compliance, and security posture of an on-prem and/or multi-cloud environment from a single dashboard.