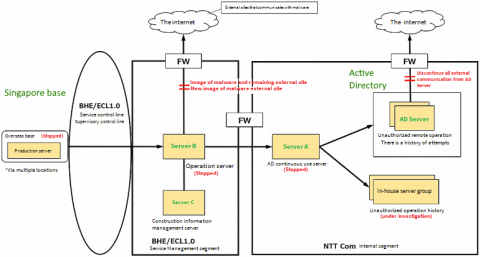
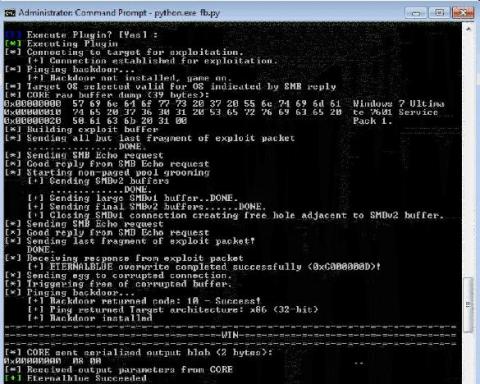
I Have Antivirus; I'm Protected, Right? Mis-steps Customers Make with their Security and Vulnerability Tools
I’ve worked in the IT field for over 30 years. 20 of those years have been spent in the network security field, employed by some of the largest names in the industry. But to my family, I’m still just the guy who “works with computers”. Many of my family are not computer savvy, which is a nice way of saying I had to teach them where the power button is. However, “Power Button Locator” is just one of my jobs. Windows won’t boot up?