Retailers Beware, Fraudulent Account Creation with Virtual Phone Numbers
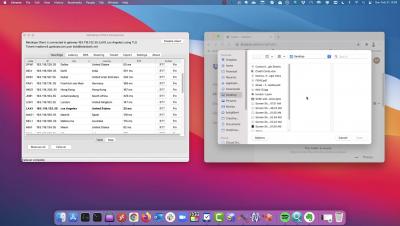
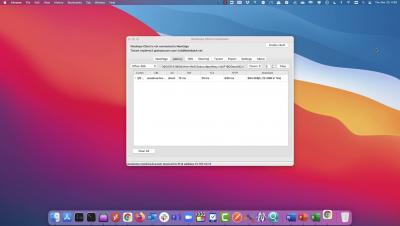
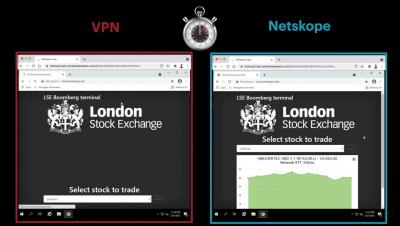
In the last couple of decades, the retail industry has seen dramatic changes, both on the business and on the consumer side. Perhaps the most notable one is buyers’ ever-increasing shift from physical “brick-and-mortar” retailers to online e-commerce platforms. Unfortunately, this has also been accompanied by more and more fraudulent activities, which in turn required for more digital checks and balances.