Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
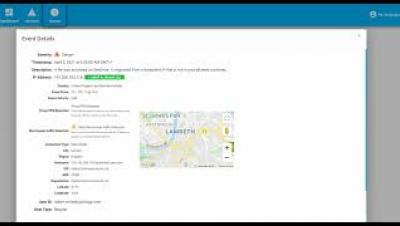
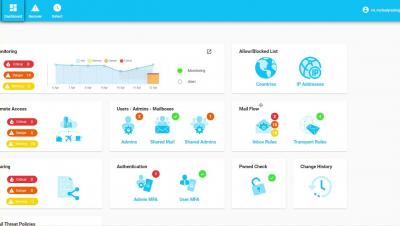
Octiga Office 365 Security Quick Demo
Critical Mobile Security Capabilities Everyone Needs
One thing that 2020 taught us is that you can do anything with a mobile device. My smartphone and tablet have become my go-to for shopping, banking, watching TV and video chatting with family and friends. I’m also getting a lot of work done on them. Basically it has become the center of both my personal and professional lives. Here’s the dilemma a lot of organizations are facing: while away from the office, your workers are using their mobile devices to stay productive.
2021 Cybersecurity: Mitigating Mobile Security Risks for CISOs
Cybersecurity has always been a significant challenge for businesses, mostly due to the increasing financial and reputational cost of data breaches. As a result, there has been a consistent rise in tactics and technologies used to combat these threats. These methods fulfill the need for better, smarter ways to augment enterprise-level security and minimize mobile security risks.
A CISO's guide to sensitive data protection
As companies become more digitized, they must take appropriate steps in their application security processes to ensure data protection. The SolarWinds software supply chain attack, which was delivered to over 18,000 customers via the company’s own software update process, was the result of malicious code deployed in SolarWinds’ Orion network monitoring software.
A Complete Guide to NIST Compliance
NIST compliance is mandatory for federal contractors, but there is a lot of confusion around it. Without it, chances of getting those big projects in the government are significantly skewed. So what is NIST compliance exactly?
5 Strategies for Safeguarding your Kubernetes Security
Since Google first introduced Kubernetes, it’s become one of the most popular DevOps platforms on the market. Unfortunately, increasingly widespread usage has made Kubernetes a growing target for hackers. To illustrate the scale of the problem, a Stackrox report found that over 90% of respondents had experienced some form of security breach in 2020. These breaches were due primarily to poorly-implemented Kubernetes security.
Building a complete network security checklist
Understanding what to audit in a network can be chaotic and confusing. Building a complete network security checklist is crucial for organizations with computers connected to the internet or to each other. Think of it like an antivirus scan you might run on your computer to find Trojans or malware, except you’re scanning your entire network to find anything that may cripple it.
AWS IAM security explained
AWS Policies are a key foundation in good cloud security, but they are often overlooked. In this blog, we take a quick look on some AWS Policies, particularly for Identity and Access Management (IAM), that could become problematic if not properly managed. We'll discuss how they can be used against us to generate attacks like: Ransomware, data exfiltration, credential abuse, and more. Finally, we'll suggest some Open Source tools for cloud policy assessment and pentesting.