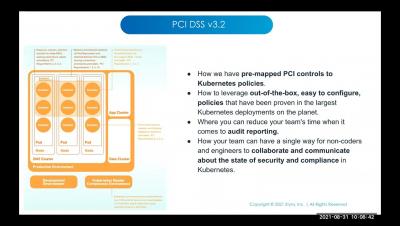
Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Snyk + Dynatrace workshop: Integrating for real-time vulnerability detection
Since 2019, Snyk and Dynatrace have partnered with a shared mission of securing the entire software development lifecycle (SDLC) and accelerating digital transformation. As many agile organizations migrate their workloads to the cloud, it’s tempting for teams to let security take a back-seat until all the pieces of the infrastructure puzzle are in place.
Happy holidays from 1Password
Arctic Wolf Cloud Detection and Response
Arctic Wolf Releases Open Source Log4Shell Detection Script
December 2021 Patch Tuesday: AppX Installer Zero-day, Multiple Critical Vulnerabilities
It’s the last Patch Tuesday update of 2021, and as with many other updates this year, this month’s list includes important ones — among them a zero-day (CVE-2021-43890 in AppX installer), multiple critical vulnerabilities and a variety of attack types utilized in several Microsoft product families — highlighting once again that patching and prioritization are prominent programs SecOps staff must regularly implement to keep adversaries from infiltrating their organizations’
Securing Microservices-Based Apps with Dynamic Traffic Authz
Weekly Cyber Security News 17/12/2021
A selection of this week’s more interesting vulnerability disclosures and cyber security news. For a daily selection see our twitter feed at #ionCube24. If you have been (luckily) hiding under a stone this week you might not be aware of a major global infosec disaster that has been on going unfolding since last weekend. As usual it is a key component included in so many other products that has a 0-day. You might want to check Twitter right away…