5 Best Practices for Risk Management
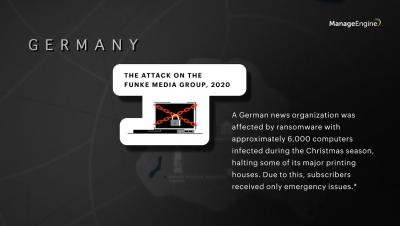
Risk management is the process of identifying, monitoring, and managing potential risks and their negative impacts on a business. These risks can range from data loss, cyberattacks, and security breaches, to system failures and even natural disasters.