What is Container Security?
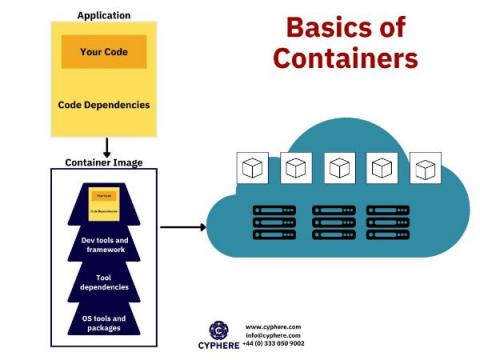
A container is defined as packaged software that contains all the code and dependencies of an application within a virtual environment so that the application can be migrated from any computing device to another. Docker container images are executable software packages that are lightweight and standalone.