Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
SOC for Cybersecurity- Everything You Should be knowing
Cybersecurity has always been a major concern for most businesses. With the growing incidents of data breaches, it is now imperative for businesses to invest their resource in securing their IT infrastructure and data. Moreover, after the COVID-19 scenario, there was an unprecedented spike in the need for remote working. This totally hampered the security measures implemented by the organization’s IT and Cybersecurity teams.
Ransomware Landscape Q2
DevSecOps monitor and decommission
This is the final article of the DevSecOps series and how it overlays onto DevOps lifecycle. In the first article, we discussed build and test in DevSecOps. In the second article, we covered securing the different components of the deploy and operate process. The final phases of the DevOps lifecycle are monitoring the deployed applications and eventually decommissioning when they are no longer needed.
How to Deploy Pods in Kubernetes?
Seamless path to Zero Trust for Texas: Lookout Receives TX-RAMP Level 2 Certification
Here at Lookout we have a long tradition of supporting the cybersecurity requirements of all levels of government in the U.S. This is why I’m thrilled to announce that we have received a Level 2 certification, the highest tier of authorization, from the Texas Risk and Authorization Management Program (TX-RAMP).
KuppingerCole rates SECUDE as outstanding in extending Microsoft Purview Information Protection (MPIP)
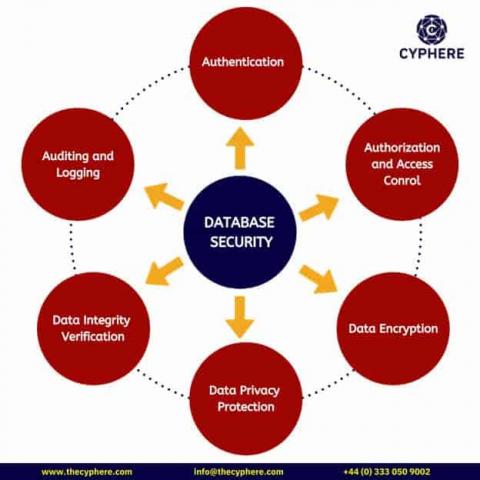
What is Database Security? Learn how to secure databases
Databases are essential for organisations because they store data critical for the organisation to function. This data can include customer information, financial records, and contact details. Organisations need to access this data quickly and securely to make decisions and run their business. A database can help them do this by providing a centralised location for all their data.