Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Top 5 Reasons Why Splunk Is the Ideal Platform for Unified Security and Observability
Splunk embodies the top 5 principles of unified security and observability, and has been an expert in log management, security, and observability for years.
The Top Cyber Attacks of August 2022
Persistence and Patience: Two Qualities You Don't Want Your Ransomware Attacker to Have
Modern organizations are built on data. It enables collaboration and helps us engage with customers. But that same helpful data is also sprawled across countless apps, making it difficult to secure. Ransomware attacks are on the rise — 57% of security leaders expect ransomware to compromise their organization within the next year — which makes data protection more essential than ever.
Addressing the Invisible Security Problem of Open File Shares
According to a recent survey from the Cloud Security Alliance, cloud issues and misconfigurations remain the leading causes of breaches and outages—and 58% of respondents report concerns about security in the cloud. Their worries are well-founded. Nearly every day, we see examples of a company’s sensitive data spilling out of leaky clouds.
Securing data through the compliance lens
MD5 vs SHA1 vs SHA2 vs SHA3 - Compare Hashing Algorithms
As the physical and digital worlds are coming together by the day, the need to protect our privacy and confidentiality is becoming more pivotal. Securing data is essential for everyone, including an organization, a person, or any digital entity. In the world of digital security, hashing and encryption are two important protection structures. Let’s keep encryption for another time and focus on hashing for today.
How to Write a Fuzz Test for JavaScript
CDN Security - How Does It Help with Website Security?
Cyberattacks have become more sophisticated, and they have the potential to cause severe disruption to service availability and financial loss to businesses. According to Gartner, IT downtime costs businesses $5,600 p/minute on average. For every business with an online presence, being able to serve user requests and deliver content in a secure, reliable, and speedy manner is critical. This is where content delivery networks (CDNs) come in.
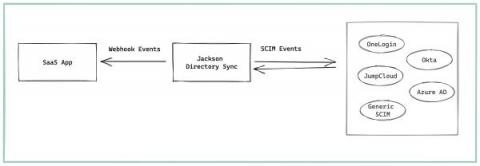
Understanding SCIM and Directory Sync
This article will walk you through everything you should know about SCIM and Directory Sync.