Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
How to Set Lock Screen Picture on Windows 10 Pro without Group Policy
Toyota data breach - Database keys exposed publically in GitHub for 5 years
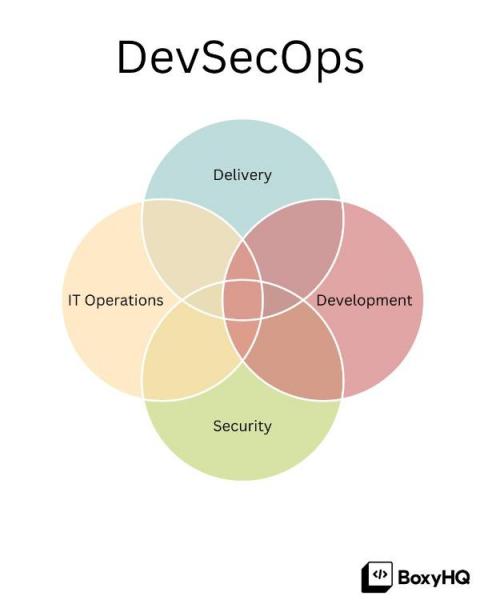
What is DevOps and how has it evolved into DevSecOps
Let's first take a look at what DevOps (Developer Operations) is so we can better understand why it has now evolved into DevSecOps (Developer Security Operations). DevOps is a combination of philosophies, practices, and tools that increases a business's ability to deliver better development in less time (Higher velocity). This can be applied to building a new product or the process of continuous improvement that applies to most products we see today.
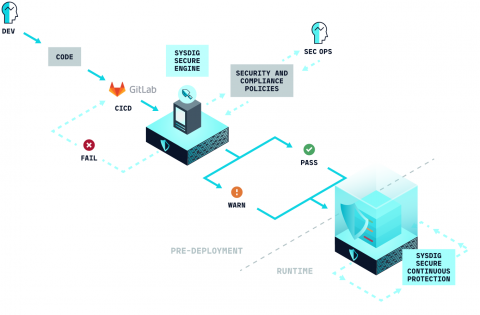
Image scanning for GitLab CI/CD
Scanning a container image for vulnerabilities or misconfigurations on your GitLab CI/CD using Sysdig Secure is a straightforward process. This article demonstrates a step-by-step example of how to do it. The following proof of content showcased how to leverage the sysdig-cli-scanner with GitLab CI/CD. Although possible, this procedure is not officially supported by Sysdig, so we recommend checking the documentation to adapt these steps to your environment.
Monitor your firewalls on the go with Firewall Analyzer's mobile app
The number of cybersecurity events faced by companies and businesses across the globe has grown exponentially since the pandemic began. Without adequate network security monitoring practices and around-the-clock monitoring in place, the chances of a cyber incident happening are highly likely. However, not all companies can afford to have a team of highly trained network admins watching over their network 24×7.
Security Basics: Incident Response and Automation
Incident response is one of the most challenging tasks that IT teams face. It's challenging not just because it typically involves many stakeholders and moving pieces, but also because teams usually face pressure to respond as quickly as possible. That's why investing in incident response automation is a wise choice. Although it may not be possible to automate every aspect of every incident response workflow, being able to automate at least the major elements of incident response will yield incident management processes that are faster, more reliable, and more consistent.Keep reading to learn about the components of incident response and which incident response activities to start automating.
Protecting DOD controlled unclassified information (CUI) from getting into the wrong hands
Money Laundering in the Metaverse: NFTs, DeFi
According to a recent analysis, 17 million Ethereum transactions between Q4 2017 and Q1 2022 were associated with both criminal and licit operations. The overall cyber money laundering activities increased by 30% in 2021 compared to 2020, with hackers laundering a total of US$8.6 billion in cryptocurrencies.
How to Boost Cybersecurity in Fintech and Banking?
Globally, fintech firms saw 2.5 times more attacks in Q1 2022. The BFSI industry is prone to cyberattacks every day. Fintech firms carry some vital data. Cybercriminals know it. They aim to exploit your system’s flaw to access the data. The worst part is they will use it for financial fraud. A successful data breach causes penalties and reputation losses. It scares away your customers. It is even motivating cybersecurity in Fintech. How do you make a secure financial platform?