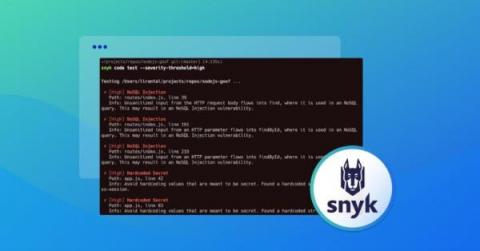
5 "no experience needed" tips for building secure applications
Most developers aren’t security experts. This isn’t because we don’t care about security, it’s just that there are only so many hours in the day and features come first. Fortunately, developers don’t need to be security experts to build secure apps — they just need the right tools.