Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
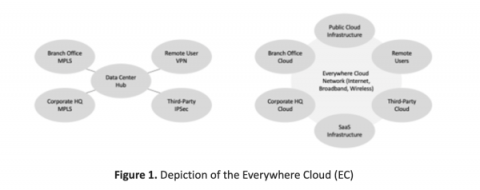
Corelight for the everywhere cloud
Editor's note: This is the first in five-part series authored by Ed Amoroso, founder and CEO of TAG Cyber, which will focuses on how the Corelight platform reduces network security risks to the so-called Everywhere Cloud (EC). Such security protection addresses threats to devices and assets on any type of network, including both perimeter and zero-trust based.
Kubescape brings a new level of security to Charmed Kubernetes
Top 15 Kubectl plugins for security engineers
Let's dig deeper into this list of Kubectl plugins that we strongly feel will be very useful for anyone, especially security engineers. Kubernetes, by design, is incredibly customizable. Kubernetes supports custom configurations for specific use case scenarios. This eliminates the need to apply patches to underlying features. Plugins are the means to extend Kubernetes features and deliver out-of-the-box offerings.
Utilizing Tines' Automation Capability Matrix
Automation is often seen as the natural progression for a security operations center. However, deciding where and when to implement it can be pretty challenging. As an earlier blog post covers, Tines' Automation Capability Matrix is an innovative set of techniques that empower security operations teams to respond proactively and tackle common cyber-security incidents.
Ransomware in the Construction Industry: How Unregulated Data Makes it a Soft Target | John Goecke
The 443 Episode 225 - The RCE Vulnerability That Wasn't
Veracode SCA Scan for VS Code Plugin
Switching Between Multiple Domains
Does Your Organization Meet the 9 Core Capabilities Essential for Zero Trust in IoT?
Every one of your IoT devices has their own machine identity. But how are these identities the key to achieving Zero Trust IoT project? Today’s PKI (Public Key Infrastructure) vendors have specific solutions for managing non-human identities – machines – like servers, laptops, software applications, API’s and other assets found within a corporate network.