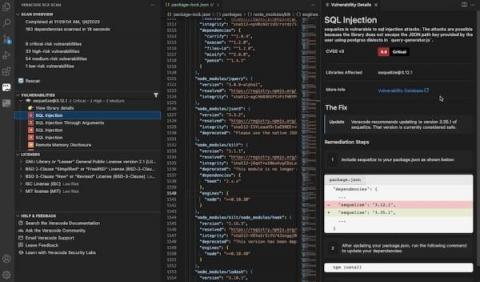
Threat detection review: Insider threats in cybersecurity
Globally, 67% of companies experience between 21 to 40 insider-related incidents per year, according to Ponemon Institute’s The Cost of Insider Threats 2022 report. The same report reveals that the frequency and cost of insider attacks have increased significantly over the past two years. Insider threats are one of the tougher attacks to predict and prevent, because of the difficulty in identifying insiders.