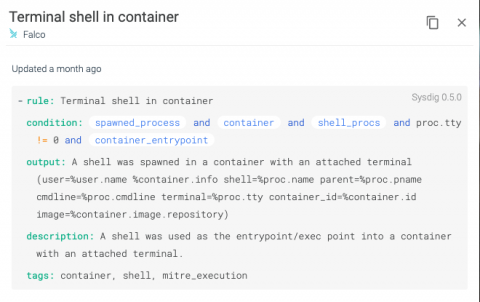
Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Verizon's 2019 Payment Security Report - Not Just for PCI
If you are responsible for cybersecurity or data protection in your organization, stop what you are doing and read this report. Actually, first, go patch your servers and applications and then read this report. Much like Verizon’s Data Breach Investigations Report (DBIR), the Payment Security Report (PSR) is a must-read for security professionals.
Universal Network-level Call Blocking: What You Need to Know
Many of the current telephone scams use caller ID spoofing to mask the identity of the caller. A few of those telephone scams spoof caller IDs that don’t match the North American standard for legitimate numbers. These blatantly obvious spoofed caller IDs are the target of the Canadian Radio-television and Telecommunications Commission (CRTC).
How to Map PCI DSS to the NIST Cybersecurity Framework
Organizations face an increasing number of compliance metrics. Risk management is of paramount importance and is feeding the need for governance. Terms like PCI DSS and NIST CSF are two frameworks that help enhance data security and manage risk. Often, it is the confusion on where businesses need to start that prevents them from taking action at all.
Modern compliance with Sysdig Secure DevOps Platform
Authorization to Operate (ATO) in a day and on-going authorization are compliance nirvana. The ATO is the authorizing official’s statement that they accept the risk associated with the system running in production environments using live business data. The idea that all of the information necessary to make a risk decision is at hand and can be consumed by decision makers is what every compliance program is trying to achieve.
What is Psychographic Data?
Psychographic data is information about a person's values, attitudes, interests and personality traits that is used to build a profile of how an individual views the world, the things that interest them and what triggers motivate them to action.
Technado, Episode 128: CyberArmor's Shauli Rozen
Climbing the Vulnerability Management Mountain: Reaching Maturity Level 2
The path is starting to get steeper now as we climb to ML2. It is time to start defining a vulnerability management program with objectives and goals. This program is expected to grow and evolve over time as the organization grows and evolves. Start by documenting what is in place now and what objections the organization is trying to reach. The stakeholders should come from multiple departments within the organization. For example, you will need buy-in from:
Zero-Day Ransomware Detection is a Necessity, Not a Luxury
No one is a stranger to the notion of security. We protect our homes and physical assets with locks and cameras and are vigilant when we encounter abnormal behavior. But for some reason, the data entrusted to us is not always given the same type of protection. That data has become a prime target for cybercriminals which is manifested in the form of ransomware attacks, which are increasingly prevalent.
What is ITIL Incident Management?
Today’s cybersecurity threats are so fast and sophisticated that they can disrupt IT functions for hours, days, and even months. For example, the ransomware attack prevents users from accessing their systems or files unless they pay a ransom to notorious extortionists. Under such circumstances, having an effective incident management program is always necessary.