Feed me!
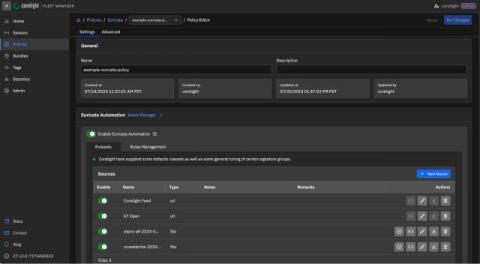
Corelight has strengthened the Suricata integration within its Open NDR Platform, empowering customers with a custom ruleset, the Corelight Feed, designed to swiftly detect and help respond to emerging threats. With a new monthly update cycle, Corelight ensures that organizations stay ahead of the latest vulnerabilities and enhance their network security posture effortlessly.