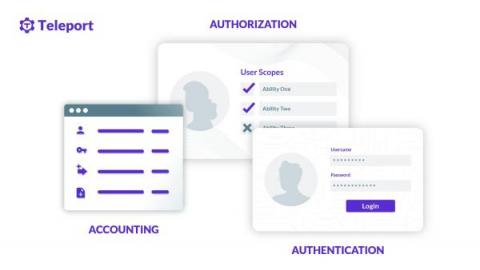
Leaving your job? Here's how to protect yourself and your employer's data
The end is in sight. You’ve decided to leave your job and have already handed in your notice. You’re finishing up some final projects and, before too long, will be saying one last goodbye to your coworkers.