OT:ICEFALL Continues: Vedere Labs Discloses Three New Vulnerabilities Affecting OT Products - How to Mitigate
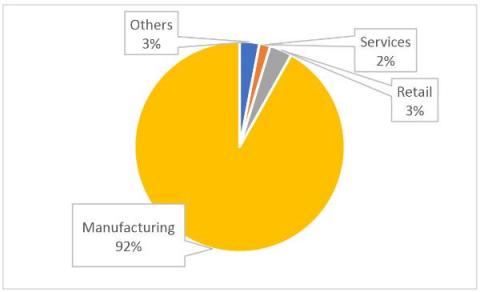
Continuing our OT:ICEFALL research, Vedere Labs has disclosed three new vulnerabilities affecting OT products from two German vendors: Festo automation controllers and the CODESYS runtime, which is used by hundreds of device manufacturers in different industrial sectors, including Festo.