Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Amazon EC2 SSH Session Recording and Auditing with Teleport
This blog is Part IV in a series about identity-based access management of AWS resources. In Part I, we covered how to use OSS Teleport to access Amazon EC2 instances running in private subnets. Part II explained implementing identity-based access via SSO integration with Okta. Part III covered the steps to configure privilege escalation for just-in-time access requests. In Part IV, we will guide you through the steps to configure SSH session recording and auditing.
The 4 most effective steps to mitigate account theft
The migration of assets to the Cloud has been the common denominator in company business strategies over the last two years, coupled with the rising number of incidents involving the theft of sensitive information and user passwords on Cloud platforms. According to the Verizon Data Breach Report 2021, in 2020 29,207 real-time security incidents were detected, out of which 5,258 were confirmed data breaches.
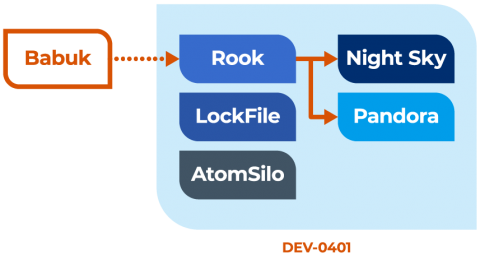
Night Sky: A Short-Lived Threat from a Long-Lived Threat Actor
In a new threat briefing report, Vedere Labs analyzes the behavior of the Night Sky malware on two samples, presents a list of IoCs extracted from the analysis and discusses mitigation. The Night Sky ransomware was first reported on January 1, 2022. Victims were asked to contact the attackers to pay for the ransom. If the victims refused to pay, attackers threatened to expose their data on a leak site.
Three Benefits Authorization Brings to your Identity Strategy
Organizations today are embracing cloud-native technologies to increase time-to-market, scalability and cost savings. A big part of the cloud-native transition is moving legacy systems and architectures to the cloud. With this comes both complexity and new risks because modern applications are often composed of dozens of microservices, housed in containers and hosted on immutable, dynamically scaling platforms like Kubernetes.
Security Doesn't Stop at the First Alert: Falcon X Threat Intelligence Offers New Context in MITRE ATT&CK Evaluation
CrowdStrike recently demonstrated the power of the Falcon platform and its integrated approach to providing robust protection by exposing all attack tactics used as part of the MITRE Engenuity ATT&CK Enterprise Evaluation released in April 2022. The evaluation focused on emulating two of today’s most sophisticated Russian-based threat groups: WIZARD SPIDER and VOODOO BEAR (Sandworm Team).
CyRC Vulnerability Analysis: CVE-2022-1271 in gzip, but it's not as bad as it sounds
Top Tips for Moving from Compliance to Cybersecurity Excellence
Compliance should be an essential part of business operations, regardless of industry. Taking preventative measures to manage compliance and mitigate risk can feel like a hassle upfront, but it can save your organisation huge costs in the long run. Compliance violations can result in fines, penalties, lawsuits, loss of reputation, and more. However, your efforts should not stop at obtaining a compliance certificate, rather they should expand to accelerate your cybersecurity posture.
What Makes Telecommunication Companies Such a Fertile Ground for Attack?
Telecommunication is the first, and most robust network ever invented. This may seem like a brazen and bold statement, but when examined closely, it is not the stuff of fantasy. Prior to the invention and development of the internet, what other way could a person pick up a device, and “dial” a few numbers and end up seamlessly connected to someone across the vast expanse of a countryside?
Eliminate noise and prioritize the vulnerabilities that really matter with Risk Spotlight
Is your team drowning in container vulnerability noise? Are you spending a lot of time figuring out where to focus resources on and still missing dangerous vulnerabilities? Know that you are not alone. Container environments revolutionized app development by enabling unprecedented velocity, but not without a price. The use of readily available container images of third-party and open-source code enabled much faster cycles, but also facilitated the introduction of vulnerabilities in the application.