Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Top Challenges Faced in the Current Cyber Security Industry
Protecting devices, data, or systems from cyber threats is what cyber security is all about. These cyber-attacks are usually aimed at gaining access to, destroying, or stealing sensitive data, or consumers’ money and disrupting online transactions and business operations. Implementing an effective cyber security system is critical, as the task has grown increasingly difficult.
Four Takeaways as the European Union's General Data Protection Regulation (GDPR) Turns 4
Chip away at age old-password problems by reinventing your security strategies
Despite wide-spread knowledge on the risk of using a weak password, 123456 is still a common password in use by a number of users. You’re probably wondering who would still use this password. Well, close to 103 million people around the world according to NordPass’ report. While this is alarming, let’s just take a moment to consider why users choose simple, easy-to-remember passwords despite being aware of the risks. Password overload: How big of a concern is it?
What is ePHI? A Guide to electronic Protected Health Information (ePHI)
ePHI stands for electronic protected health information. Electronic protected health information is protected under the Health Insurance Portability and Accountability Act of 1996, commonly known as HIPAA. ePHI security is governed by the HIPAA Security Rule. With the rise of telehealth, covered entities need to understand the requirements for safely transmitting, storing, and using ePHI to be compliant with the Security Rule and to protect a patient’s privacy.
What is the difference between a vendor and a third party vendor?
A manufacturing organisation providing direct goods and services is known as a vendor. If the same services and products are provided on behalf of a direct vendor, they are known as third-party vendors. Third-party vendors always have a direct written contract, but not each vendor and organisation works with contracts. The definition of an entity as a third-party vendor depends on the organisation hiring its services.
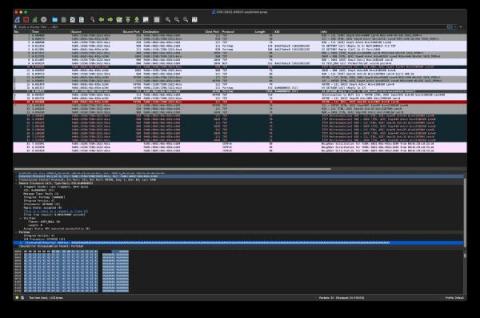
Detecting CVE-2022-26937 with Zeek
This month, Microsoft announced a vulnerability in NFS. The exploit lies in how an attacker can force a victim NFS server to request an address from the attacker’s fake NFS server. The address returned will overflow memory on the victim NFS server and cause a crash. Through Microsoft’s MAPP program, Corelight Labs reviewed a proof-of-concept exploit for this vulnerability and wrote a Zeek®-based detection for it. You can find a PCAP of this exploit in our GitHub repository.
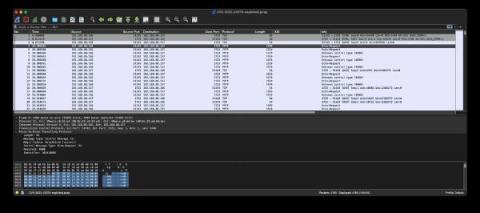
Detecting CVE-2022-23270 in PPTP
This month, Microsoft announced a vulnerability in PPTP, a part of the VPN remote access services on Windows systems that runs on port 1723/tcp. Through Microsoft’s MAPP program, Corelight Labs reviewed a proof of concept exploit for this vulnerability and wrote a Zeek®-based detection for it.
Cybersecurity Compliance and Regulations in South Africa: What Businesses Need to Know
With the Internet's widespread growth, South Africa has become quite dependent on it for economic affairs. This sharing of self-generated data is a boon to all business transactions and even social interactions. The increased dependence on the digital world raises significant concerns about cyber security. Cybercrime is a global problem that has affected South Africa, both in the private sector and in government.
Quadrant Knowledge Solutions Names CrowdStrike a Leader in the 2022 SPARK Matrix for Digital Threat Intelligence Management
We are excited to announce Quadrant Knowledge Solutions has named CrowdStrike as a 2022 technology leader in the SPARK Matrix analysis of the global Digital Threat Intelligence Management market. Among all 28 vendors in the report, CrowdStrike received the highest score in the Technology Excellence category. The SPARK Matrix evaluates top vendors in the Digital Threat Intelligence Management space on a variety of criteria and groups them into Leaders, Challengers and Aspirants.