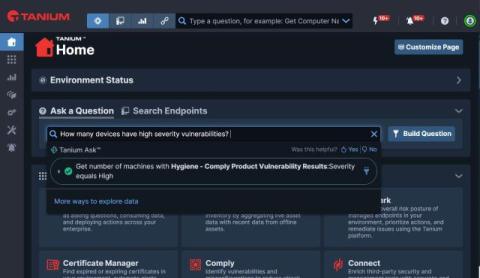
Telemetry: What It Is and How it Enables Security
If you have ever built a LEGO set, then you have a general idea of how telemetry works. Telemetry starts with individual data points, just like your LEGO build starts with a box of bricks. In complex IT environments, your security telemetry is spread across different technologies and monitoring tools, just like in a large build your LEGO bricks come separated into smaller, individually numbered bags. In both cases, the individual bricks or data points aren’t special.