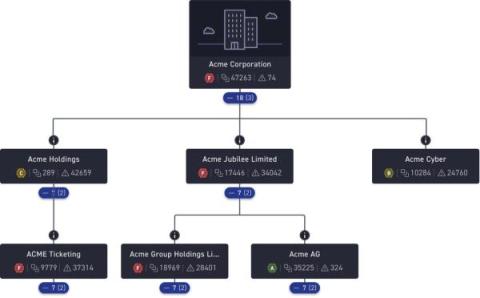
Proactive Measures to Prevent Data Theft
As the world becomes more and more digitally intertwined, the significance of data security cannot be overstated. Data theft, a critical threat to organizations worldwide, poses severe challenges, jeopardizing both reputational integrity and financial health. This blog post aims to dissect the concept of data theft, understand its impacts on organizations, and outline proactive measures to safeguard against such threats.