The 6 Best Secure Cloud Storage Services in 2024
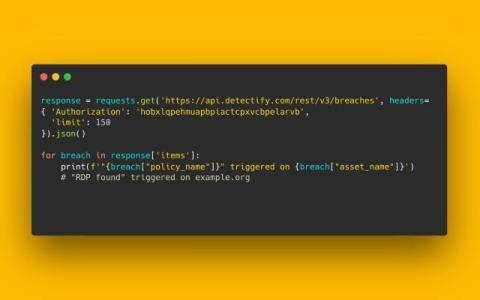
Data breaches, leaks, hacks, and compromised passwords pose a real threat to our data. If you don’t take action to protect your sensitive data, you are leaving your information exposed to hackers who could: Although many data breaches occur due to factors outside your control, it’s still important to protect your data to avoid it falling into the wrong hands. The best way to do this is by choosing from the numerous secure cloud storage services in 2024.