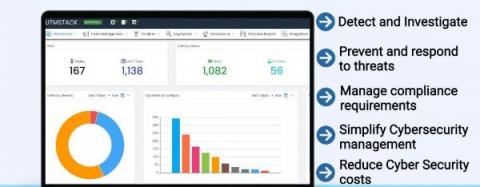
46 days vs. 16 minutes: Detecting emerging threats and reducing dwell time with machine learning
Machine learning (ML) detections are a powerful tool for detecting emerging threats when we don’t yet know what we’re looking for. The power of anomaly detection is the ability to detect and provide early warning on new threat activity for which rules, indicators, or signatures are not yet available.