Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Maintaining Security Consistency from Endpoint to Workload and Everywhere in Between
In today’s fast-paced world, mobility, connectivity and data access are essential. As organizations grow and add more workloads, containers, distributed endpoints and different security solutions to protect them, security can quickly become complex. Modern attacks and adversary tradecraft target vulnerable areas to achieve their objectives. Threats can originate at the endpoint to attack the cloud, or cloud-based threats can attack vulnerable endpoints.
Splunk Indexer Vulnerability: What You Need to Know
A new vulnerability, CVE-2021-342 has been discovered in the Splunk indexer component, which is a commonly utilized part of the Splunk Enterprise suite. We’re going to explain the affected components, the severity of the vulnerability, mitigations you can put in place, and long-term considerations you may wish to make when using Splunk.
Cybersecurity Risk Management: Introduction to Security Analytics
Article 28 - General Data Protection Regulation Act
The General Data Protection Regulation Act (GDPR) requires Data Controllers to establish a written agreement with the Data Processor stating the terms and conditions for the data processing activity. So, before getting into a contract with the Data Processor, a Data Processing Agreement must be signed between both parties regarding the conduct of processing personal data.
Formulating proper data destruction policies to reduce data breach risks
As Morgan Stanley Bank now knows, ignoring certified data destruction policies can be disastrous. The bank made news in 2020 when it was fined over $60 million for not using proper oversight when decommissioning two of its data centers. Regulators found that the organization had not addressed the risks associated with decommissioning hardware effectively.
SIEM Use Cases for Compliance with GDPR
The era we live in requires the digitalization of all subjects interacting with people, from giant companies to small-scale organizations. It is unquestionable that this trend has made significant contributions to the data collection process. But the larger the volume of data collected, the greater the risk of a security breach. For this reason, it is essential to control the security and transparency of personal data.
Five Steps to Protect Your Organization against Phishing Attacks
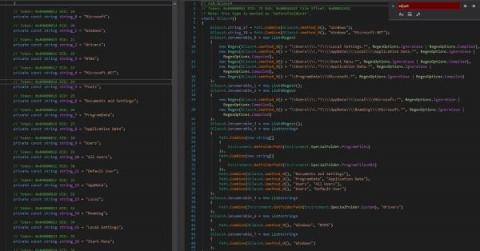
Threat Update DoubleZero Destructor
The Splunk Threat Research Team is actively monitoring the emergence of new threats in the cyber domain of ongoing geopolitical events. As we have shown previously in several releases, including HermeticWiper and CaddyWiper, actors in this campaign are deploying, updating, and modifying stealthier malicious payloads. On March 17th, 2022, the Ukraine CERT discovered a new malicious payload named DoubleZero Destructor (CERT-UA #4243).
Working with At-Risk Businesses: How It Can Dismantle Your Zero Trust Strategy
Nowadays, building a zero-trust network has become a standard protocol in the era of evolving business models, multiple workforce platforms, cloud adoption, and increased device connectivity. But, if a business continues to work with at-risk organizations, the zero-trust policy crumbles. Working with well-secured third parties that uphold a zero-trust strategy is crucial for optimal cybersecurity within any business.