From Alerts to Action: How AI Empowers SOC Analysts to Make Better Decisions
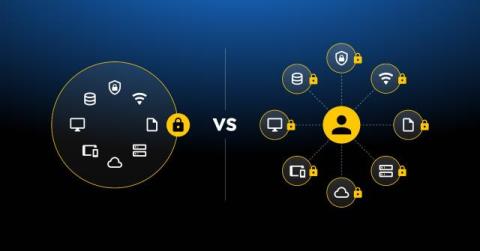
Security Operations Center (SOC) analysts have it rough. Modern security tools generate an extraordinary number of alerts, attackers are more sophisticated than ever, and IT infrastructures are unprecedentedly complex. As a result, analysts are overwhelmed with workload and alerts, making it near-impossible to make intelligent, informed decisions. Fortunately, artificial intelligence (AI) is helping to ease the strain. Let’s look at how.