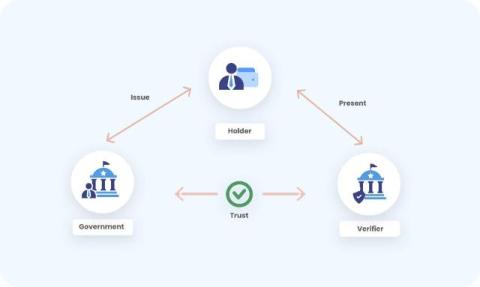
2025 Predictions
With 2025 just around the corner, we have once again reached out to our deep bench of experts to read the tea leaves and give us a sense of the trends and themes that they expect to see emerging in the new year. Here’s what the Netskope experts think is in store for next year.