Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
The secret is out: Why Open Security is key to preventing cyber threats
6 Use Cases for Distributed Deep Learning
In the world of Big Data, decentralization is king. Seeing that today’s data sets are so large and complex that traditional database systems cannot handle them, distributed deep learning splits computational problems that require high storage and solving time into many subproblems that can be assigned to multiple machines.
Reducing Risks of Real-Time Payments Adoption
2023 might be a really important year for real-time payments (RTP) development in North America. FedNow, a real-time payments service, is on track to go operational in 2023 in the USA, while the Real-Time Rail (RTR) payment system will be fully launched in Canada, also in 2023. Currently, in their test phases, these payment systems will go mainstream next year, making faster payments more accessible to smaller financial institutions and businesses.
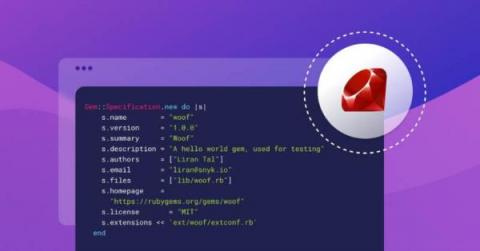
Ruby gem installations can expose you to lockfile injection attacks
In this post, we’ll look at the security blindspots of lockfile injection that a Ruby gem might expose via its Gemfile.lock. As a prelude to that, we will open up with a brief introduction to Ruby and third-party dependencies management around RubyGems and Bundler. Web developers often work on Ruby projects, but are mostly referring to them as the popular open source web application framework Ruby on Rails.
Introducing Kojensi SaaS v2.0 with New Export Control Material Capability for ITAR
3 Security Lessons We Haven't Learned From the Kaseya Breach
Understanding cyber security vulnerabilities
Every other day, a new cybersecurity breach compromising common or 0-day vulnerability is reported. The rapid shift of digital businesses and remote work opened a whole arena for cyber attacks and increased the demand for solid defences. But, to stay ahead of adversaries, it is critical that you know what cyber security vulnerabilities are after too.
Cyber Security Compliance
Usually, IT professionals and newcomers to the information security domain confuse security and compliance, which is not their fault. Both are to protect individuals’ and businesses’ digital and physical assets through appropriate security measures.
The Evolution of Application Security in a Cloud-Native World: Q&A with Chris Wysopal
As technology explodes, so do the threats. Point solutions emerge as security players innovate in order to keep up. This creates the need for consolidation, as the fragmented solutions become too much to manage. We’re entering a consolidation phase now, the process of distilling, refining, and letting the cream rise to the top. We sat down with cybersecurity veteran and vigilante, Chris Wysopal, to get his perspective on emerging trends in cloud-native security.