Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Expose and Disrupt Adversaries Beyond the Perimeter with CrowdStrike Falcon Intelligence Recon
Cybercriminals continuously adapt to stay a step ahead of the organizations they target. Over more than a decade, CrowdStrike has carefully tracked the evolution of eCrime tactics and capabilities and codified them in more than 4,900 intelligence reports. Today’s threat landscape is dominated by sophisticated ransomware operators and data extortionists that are supported by a robust and increasingly specialized market-based ecosystem of criminal service providers.
A New Approach to Data Security for the New Year
Over the last few years, we have seen more and more organizations moving into hybrid and remote working environments. With that change, IT teams have learned that they cannot trust the network like they have in the past. Using the internet, employees now have direct access to your organization's resources, circumventing traditional security tools like virtual private networks (VPNs) and firewalls.
Malicious Use of Signed Drivers in Microsoft Windows
How to deal with cyberattacks this holiday season
The holiday season has arrived, and cyberattacks are expected to increase with the upcoming celebratory events. According to The Retail & Hospitality Information Sharing and Analysis Center (RH-ISAC) 2022 Holiday Season Threat Trends and summary report, ransomware and phishing attacks are expected to increase in retail. With the FIFA World Cup 2022, many cybersecurity experts have advised heightened caution about online impersonation scams and phishing campaigns.
Operation Power Off: 50 DDoS-services taken offline in international crackdown
Law enforcement agencies in the United States, UK, Netherlands, Poland, and Germany have brought down the most popular DDoS-for-hire services on the internet, responsible for tens of millions of attacks against websites. 50 of the world's biggest "booter" sites used to launch disruptive distributed denial-of-service attacks have been taken down as part of "Operation Power Off" - a joint action by the US Department of Justice, FBI, the UK's National Crime Agency, and their equivalents.
4 Cloud-Native Predictions for 2023
As AuthZ Becomes Mainstream, Policy as Code, Infrastructure as Code and Software Supply Chain Security Will Merge It’s the holiday season, which means it’s time for the greatest gift of all: next year’s predictions. Last year, we predicted that in 2022 security teams will embrace cloud-native tools to automate manual checks, that enterprises will increasingly shift on-prem resources into the cloud and that we’d see the emergence of a clear authorization market.
Snyk in 30: Open source security for Atlassian Bitbucket Cloud
In our latest Snyk in 30, Jason Lane (Director of Product Marketing) and I (Marco Morales, Partner Solutions Architect) showcased Snyk Open Source with a focus on our integration with Bitbucket Cloud. They covered why open source security is vital for modern app development, along with tips on taking a holistic approach to application security that goes beyond just shifting left.
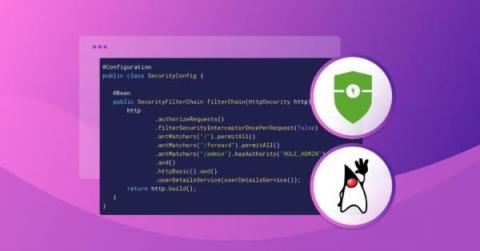
Exploring the Spring Security authorization bypass (CVE-2022-31692)
In early November, a new authorization bypass vulnerability was found in Spring Security 5. Now, before we panic let’s look into this problem to see if you are vulnerable. Although the vulnerability is classified as high, there is only a specific set of use cases that are vulnerable. This means that not everyone is vulnerable, and I will show that in a second. Regardless, the advice is to upgrade to the newer version of the Spring Security.
Corelight Demo Data Now in Falcon LogScale Community Edition
At CrowdStrike, we’re always looking for new ways to share the power of CrowdStrike Falcon® LogScale, our log management and observability solution. The latest advancement to Falcon LogScale, previously known as Humio, is adding Corelight demo data to the Falcon LogScale Community Edition.