Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
How to value a business
The remote IT workforce boom and ways to face it
Bid goodbye to ransomware attacks with Endpoint Central's Anti-Ransomware
Ransomware is an alarming cyberthreat that’s been evolving over the decades. According to Statista, there were a total of 236.1 million ransomware attacks worldwide during the first half of 2022. When organizations do not pay attention to their company’s cybersecurity structure, attackers instigate ransomware attacks by encrypting confidential files and folders, and ultimately demanding ransom. The ransom varies according to the type of ransomware variants.
Why Choose Penetration Testing as a Service?
For companies looking to stay ahead of the ever-evolving cybersecurity landscape, penetration testing is one of the most important services they can invest in. Penetration Testing as a Service (PTaaS) provides businesses with an effective way to identify security vulnerabilities before they become major issues and cause irreversible damage.
Understanding Malware-as-a-Service (MaaS): The future Of cyber attack accessibility
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. With the explosive growth of technology, businesses are more vulnerable than ever to malicious cyber attacks. And as cybercriminals become more sophisticated, new methods of attack are popping up left and right.
Customer Onboarding: Digital Identity Management in 2023
This year, 2023, digital identity verification will take on greater urgency. This is largely due to the fact that fraudsters stole more than $11.4 billion through account takeovers (ATOs) last year, while account origination fraud is predicted to cost $5 billion by 2024. The world of technology and everything linked with it moves at a breakneck pace. Identity verification is no exception.
How to password protect your PDF files
PDF files have become an essential part of our digital lives. We use them to create and share invoices, reports, contracts, and countless other documents every day.
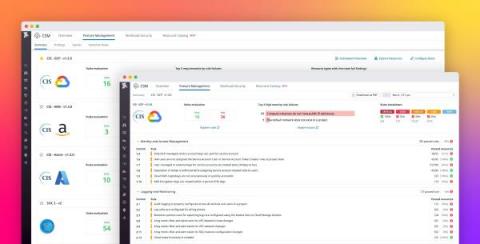
Improve the compliance and security posture of your Google Cloud environment with Datadog
Organizations are scaling their environments at a rapid pace, deploying thousands of cloud resources, services, and accounts. Because of their size and complexity, these environments are more susceptible to compliance issues—a misconfiguration in a single cloud resource can lead to costly data breaches. For that reason, organizations are prioritizing governance, risk, and compliance (GRC) management to ensure that their environments are configured appropriately.
Securing Lawyers and In-House Legal Teams from Cyber Risks
Whether they’re part of a law firm or in-house counsel within a company, lawyers handle sensitive information every day. That alone makes them prized targets for cybercriminals. The American Bar Association’s 2021 Technology Survey Report found that 25% of lawyers in the United States have experienced a data breach before.