Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Ransomware Trends 2023, Q2 Report
5 Things Everyone Needs to Know About GRC
Over the following years, the costs associated with cybercrime, projected at $10.5 trillion annually by 2025, will exceed the estimated worldwide cybersecurity spending—$267.3 billion annually by 2026. Leadership needs to change its perspective on managing cyber risks instead of just spending more money to match the losses incurred.
What is a YubiKey? How Does it Work? [Detailed Guide]
Aren’t you a tech junkie? It does not matter anymore with YubiKey! But you must be thinking about how. This comprehensive guide dedicated to Yubikey will describe and update every necessary detail. As a reader, you must seek a one-stop solution for all your needs and asks about this device. And we have made sure to be mindful of it and curate content below that can surely answer your questions and doubts.
From Paper to Digital: Transitioning to OCR Bank Statements
Banks and other financial organisations must digitise their information for quicker storage and retrieval as they process millions of client papers annually. An developing technique called optical character recognition (OCR) makes it possible to extract data from PDFs and photos and convert them to Excel, CSV, and other formats. With the use of OCR, banks can swiftly extract client information from PDF documents, transform it, and make it searchable.
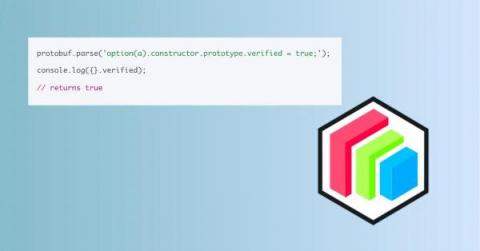
New Vulnerability in protobuf.js: Prototype Pollution - CVE-2023-36665
Did Your Password Leak Online? And What To Do About It
Cloud Defense in Depth: Lessons from the Kinsing Malware
In the face of persistent data breaches and escalating cyber threats, organizations are compelled to prioritize cloud defense in depth. These measures are indispensable for protecting critical assets and upholding the integrity of cloud-based systems. By establishing a comprehensive security plan, organizations can effectively convey their commitment to security and lay a solid foundation for a resilient and secure cloud environment.
What is a cloud migration and why do you need one?
In the past, organisations traditionally stored their data, applications, and resources in on-premises servers located in their building and typically managed by an in-house IT team. However, the modern work landscape has changed significantly, many businesses now prefer to migrate their IT infrastructure from on-premises to servers that are hosted and accessed through the internet, also known as ‘The Cloud’.
Cato's 5 Gbps SASE Speed Record is Good News for Multicloud and Hybrid Cloud Deployments
In the original Top Gun movie, Tom Cruise famously declared the words, “I feel the need! The need for speed!” At Cato Networks, we also feel the need for speed, and while we’re not breaking the sound barrier at 30,000 feet, we did just break the SASE speed barrier (again!).