Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Malicious URLs In Phishing Emails: Hover, Click and Inspect Again
The most often recommended piece of anti-phishing advice is for all users to “hover” over a URL link before clicking on it. It is great advice. It does assume that the involved users know how to tell the difference between rogue and legitimate URL links. If you or someone you know does not know how to tell the difference between malicious and legitimate URL links, tell them to watch my one-hour webinar on the subject. We are going to recommend a slight update on the rule.
Senior Executives Beware: The Rise of EvilProxy Phishing Campaigns
Menlo Security warns that a social engineering campaign is using the EvilProxy phishing kit to target senior executives across a range of industries, including banking and financial services, insurance, property management and real estate, and manufacturing.
New Gartner Forecast Shows Global Security and Risk Management Spending to Increase by 14% in 2024
Gartner issued a press release that forecasted global security and risk management end-user spending to reach $188.1 billion, along with worldwide end-user spending on security and risk management projected to be $215 billion in 2024.
Exploring the Future of Business-Led Development: Highlights from Microsoft Power Platform 2023 Conference
In an era where humans are becoming closer and closer to technology, it is reshaping the way we work and do business. This was a prevalent theme from the Microsoft Power Platform 2023 conference, and it was great to experience the event as it provided insight into the cutting-edge tools and strategies driving the next wave of business productivity.
Detecting and mitigating CVE-2023-4911: Local Privilege Escalation Vulnerability
Recently, Qualys discovered and reported a critical vulnerability affecting the popular GLIBC ecosystem, which is installed by default on most Linux-based operating systems. Specifically, a buffer overflow was found in the code responsible for handling special environment variables during the startup of a process which can result in a local privilege escalation. Fortunately, exploitation of this vulnerability can be detected by Falco.
How Sysdig can detect Impersonation Attacks in Okta IdP
To combat the growing threat of identity attacks, organizations need to adopt a proactive approach that goes beyond traditional security measures. Identity Threat Detection and Response (ITDR) is one such approach that focuses on monitoring and responding to suspicious activities related to user identities and access management. ITDR solutions can help organizations spot unusual patterns, such as multiple failed login attempts, access from unusual locations, or abnormal behavior within the system.
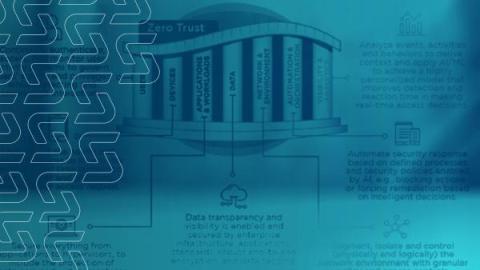
What is Zero Trust
Zero Trust is a cybersecurity philosophy that rejects the idea of offering implicit trust to traffic based on network location. In other words, Zero Trust views all traffic as potentially malicious, regardless of whether it originates from a traditionally trusted network source, and therefore requires all traffic to be scrutinized to determine whether access should be granted to a specific resource.
451 Spotlights Keeper Security for Cloud-Native Approach and Focused Vision
Keeper Security’s Privileged Access Management (PAM) solution, KeeperPAM™, has been featured by 451 Research, a technology research firm that provides an unbiased view of opportunities and risks across the enterprise technology landscape. The 451 Research group is part of S&P Global Market Intelligence.
How To Manage Passkeys
You can manage your passkeys by storing them in a password manager that supports them. By storing your passkeys in a password manager, you’ll ensure that you can access and manage them from any device. Continue reading to learn how a password manager makes managing your passkeys a seamless experience.