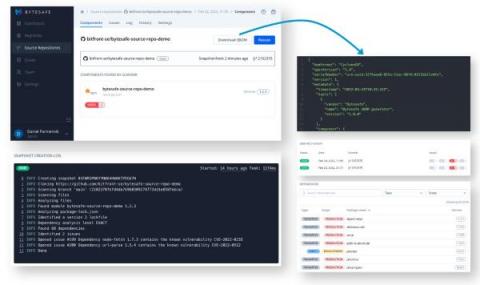
Export and Distribute SBOMs Directly From Your Git Repositories
Guest Blog by Daniel Parmenvik – CEO of bytesafe.dev For many, Software Bill of Materials (SBOMs) have changed from a manual list of assets for due diligence procedures to become an integral and automated part of software development. The ever increasing appetite for open-source software translates into a need to keep track of software assets (or open-source dependencies) for all applications, at any given point in time.