Cybersecurity in education, key for 1 out of 10 partners
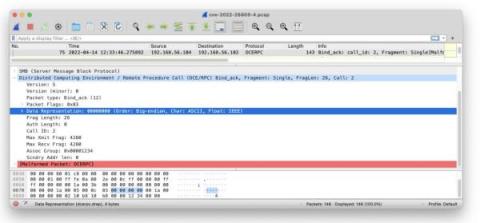
A few weeks ago, we reported how the new wave of phishing that uses new variants of COVID-19 as bait had hit the education sector hard. Many students at universities and colleges across the United States were victims of phishing attacks via emails pretending to be from administrators at their institutions.