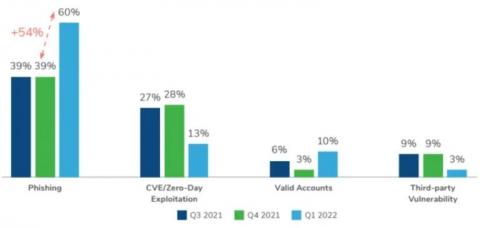
What is the HIPAA Security Rule?
Title II of the Health Insurance Portability and Accountability Act of 1996 (HIPAA) has two key provisions: the Privacy Rule and the HIPAA Security Rule. The Privacy Rule establishes standards for protecting certain health information, or PHI. The Privacy Rule requires those organizations that are governed by HIPAA (covered entities) to implement safeguards to protect the privacy of PHI, and gives individuals the right to access and share their health records.