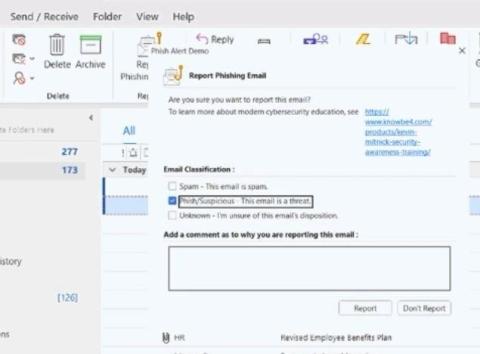
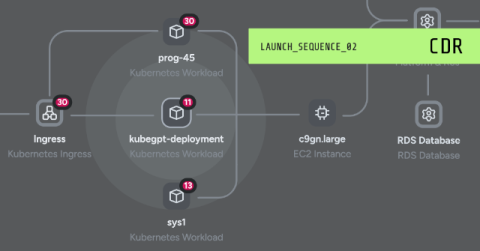
Get to Know MXDR: A Managed Detection and Response Service for Microsoft Security
The Microsoft 365 E5 license gives users entitlements to numerous Microsoft Security products—so many, in fact, that as companies deploy the Microsoft Security suite, they may need a managed detection and response (MDR) service to get the most out of it. Enter Trustwave Managed Extended Detection and Response (MXDR) for Microsoft, an MDR service built specifically for Microsoft Security customers.