How to Enhance Ubuntu Security: Advanced Features and Techniques
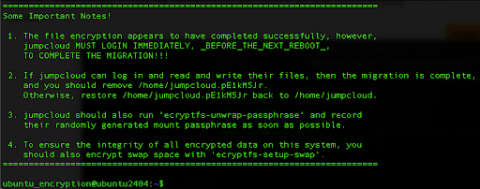
Jump to Tutorial Ubuntu, a popular Linux distribution, is known for its robust security features. There is always space for improvement once you install a fresh operating system, so in this article, we will guide you through the advanced techniques and features to enhance the security of the latest Ubuntu 24.04 version. There are multiple layers of security that Ubuntu offers out of the box, but we can implement additional steps that can further protect your system from threats.