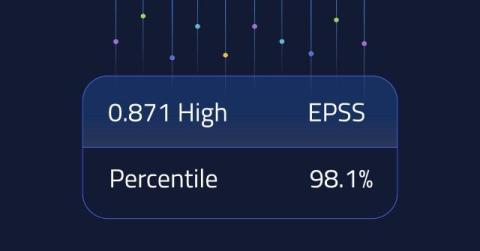
8 Daily Practices to Avoid Cybersecurity Burnout
Burnout happens when job demands such as workload, time pressure, and difficult clients are high, as well as when job resources, including quality leadership, autonomy and decision authority, recognition, and strong relationships, are lacking. The field of cybersecurity is particularly difficult, but that doesn't mean burnout is inevitable, and it doesn't mean you can't recover after experiencing burnout.