Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
New Survey Reveals Misalignment on Zero Trust Initiatives Between Management, IT, and Security Practitioners
13 reasons Log360 is the SIEM solution for you: Part 2
Our integrated compliance management tool helps you breeze through audits. Log360 provides out-of-the-box templates to meet all the major compliance regulations, such as the GDPR, PCI DSS, FISMA, HIPAA, and GLBA. What’s more, you can monitor the compliance status for these regulations in real time on graphical dashboards. Log360 also provides prebuilt compliance alerts to notify you about any critical compliance-related events.
Kong Mesh and Styra DAS - securing modern cloud-native applications
Back at KubeCon North America 2017, many speakers declared that 2018 would be “The Year of the Service Mesh”. Just a year later, in the 2019 CNCF Survey1, it was reported that 18% of surveyed organizations were using a service mesh in production, and by 20202 (the most recent survey published at the time of this writing) that number rose to 27%.
Security Automation Priorities and Challenges: How Do You Compare to Your Peers?
ThreatQuotient’s new survey on the State of Cybersecurity Automation Adoption is now available for download. Conducted by independent research organization, Opinion Matters, the survey includes responses from 250 senior cybersecurity professionals representing the following industries: central government, defense, critical national infrastructure (energy and utilities), retail and financial services.
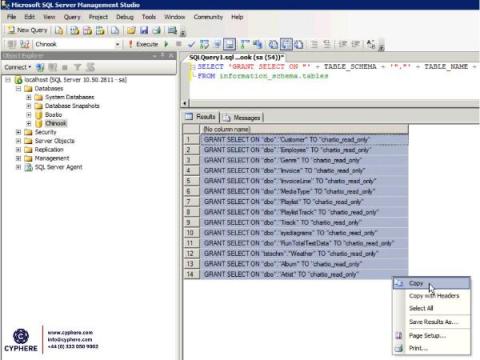
SQL Server Security: Best Practices 2021
In today’s world where digital data is increasing exponentially by the day, the administration and querying of that data are also becoming more and more complex. This huge amount of data is stored in the form of collections within a database. However, in order to create, read, update or delete that data, the database administrators needed the ability to query the database.
Low-Code SDLC - Build Fast, Stay Secure
Low-code application development provides a solution for a wide range of business needs, from business applications through process automation and integrations. Low-code platforms are becoming a key technology behind the ongoing digital transformation trend, and as such, adoption of low-code platforms is soaring. However, low-code is as much a revolution as it is an exciting new technology.
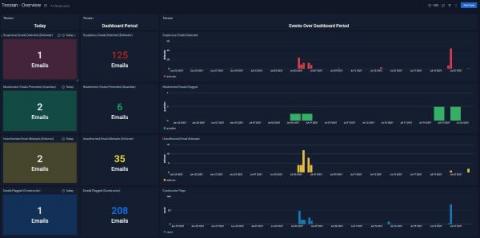
Analyzing Human Layer Risks with Tessian
Getting Networking Right in the SASE Era
In 2019, when the term Secure Access Service Edge, or SASE, was first coined, it was to define a useful way of setting up the network and security infrastructure to satisfy a cloud-first future with services at the edge. Since then, SASE has been long on hype and discussion, but short on actual, practical advice. What does SASE mean for your digital transformation strategy?
Analysis of a Parental Control System
Canopy was advertised to me through my child’s school. The company offers a multi-platform parental control app claiming various abilities to limit and monitor use of protected devices. Access to Canopy is billed monthly and includes a compelling list of features for concerned parents: Several of these features imply that the app has privileged access to the protected device and may be intercepting TLS connections to filter content.