Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
vxIntel Joins Arctic Wolf to Boost Detection and Threat Intelligence
Passwordless Authentication with Windows Hello for Business
Passwords are everywhere — and nobody likes them. For users, they are a pain to remember and manage. For businesses, they continue to be a primary source of data breaches, both on premises and in the cloud. In fact, the 2022 Verizon DBIR reports that credential theft was involved in nearly half of all cyberattacks, including third-party breaches, phishing attacks and basic web application attacks.
Integrating Snyk Open Source C/C++ security scanning into CI pipelines
Snyk Open Source supports C and C++ scanning for vendored open source dependencies via CLI — and we are happy to share that it is now available via our CI plugins as well. This guide will walk you through integrating C/C++ security scanning within pipelines to get vulnerability information and remediation advice directly to developers. Note that in the scope of this guide, we’ll refer to “C/C++” as just “C++”
Smart home under fuzzing
When To be Suspicious About Work-From-Home Employees (or Not)
Perhaps someone doesn’t answer a Slack message as quickly as they should, or they have long hours blocked on their calendar. Maybe someone doesn’t seem motivated during team meetings or they are slow to complete work. While research has shown that overall, productivity has actually increased as a result of the work-from-home movement, managers know all too well what it’s like to be suspicious that someone is taking advantage of their new work arrangement.
Warning issued about Vice Society ransomware gang after attacks on schools
A ransomware gang that has been increasingly disproportionately targeting the education sector is the subject of a joint warning issued by the FBI, CISA, and MS-ISAC. The Vice Society ransomware group has been breaking into schools and colleges, exfiltrating sensitive data, and demanding ransom payments. The threat? If the extortionists aren’t paid, you may not be able to unlock your encrypted files, and the attackers may leak the information they have stolen from your servers online.
Cyber Security Trends: The Evolving Nature of Cyber Security
Following on from the previous article we posted regarding cyber security trends, we thought we’d revisit the topic and continue with another set to keep an eye on. The world of cyber security is always evolving and there’s always too much for just one article on the subject.
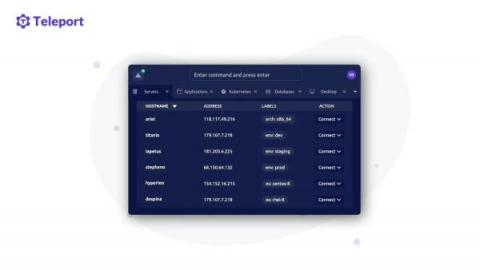
Teleport 10.2 - Teleport Connect for Windows and Directory Sharing
Teleport 10.2 was released on September 6th along with a lot of new features, bug fixes and improvements. This blog post will focus on two new features that deserve a deeper dive.
Cookie for a Thought - How to Manage HTTP Sessions
Whether it's password or passwordless authentication, multi-factor authentication, or any of the other identity verification shenanigans, in the end, our identity is deduced to a single session cookie! We can't deny the security importance of session cookies in web application access control.