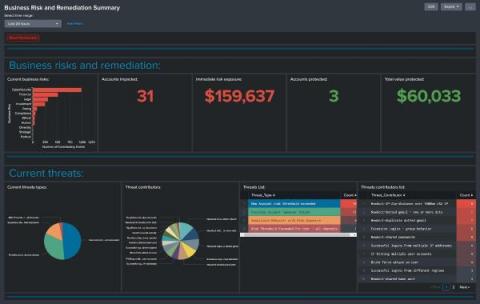
What do financial services look for in an MSP?
Data and money are two of the key assets that any industry needs to protect, and this is particularly important for financial institutions. Defending financial services against cyberattacks can be managed internally by relying on the organization's own systems; however, relying on an external cybersecurity provider offers a number of advantages that make a difference in the event of an attack.