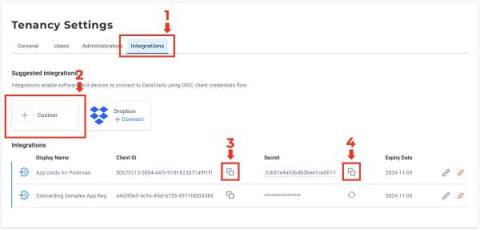
Postman Configuration for DataTrails
One of my favourite tools for playing with REST APIs is, of course, Postman. It can make interacting with DataTrails super quick and easy, and help you develop custom workflows for storing and validating your digital provenance and audit trails. Here’s a step-by-step guide to getting a robust Postman set-up configured, and if you head over the Postman public collections you’ll find a link to a pre-baked DataTrails Postman collection with this done for you, along with some example requests.