Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
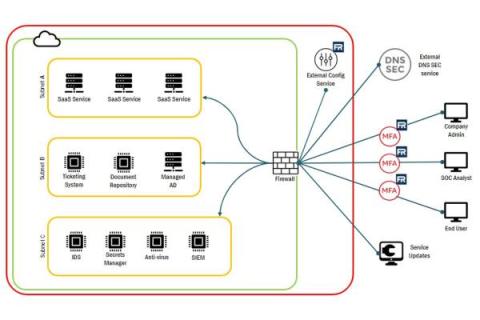
Understanding FedRAMP System Boundary
In the ever-changing world of technology, staying secure is a top priority for many organizations. Identifying and documenting system boundaries is essential for keeping data safe and secure, but what does this mean? In this article, we’ll explore FedRAMP System Boundary, how to identify them, and how to generate FedRAMP System Boundary diagrams.
New in Vanta | May 2023
In May we announced Vanta Workspaces for customers with multiple business units, improved navigation bar labels & groupings, 15 new integrations, and more.
The Roadmap to Securing Your Digital Assets with Cybersecurity
“Technology trust is a good thing, but control is a better one.”
Risk Registers: The Ultimate Guide with Examples & Template
Effectively utilizing a risk register allows your organization to anticipate and overcome challenges with confidence. No GRC program is failproof, which is why it’s so critical to take a thorough look at potential risks and remediations. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a better understanding of what it does.
Why Is CMMC a Big Deal?
The Cybersecurity Maturity Model Certification (CMMC) has been around for a few years. And, in its short tenure, it has, itself, matured. The current version of the CMMC is 2.0, released in November 2021. In the latest version of the model, the original five-level model hierarchy was collapsed into three distinct levels: Foundational, Advanced, and Expert.
How to Make the Business Case for ISO 27001 Compliance
As a CIO at a mid-sized company, I faced a new challenge when vendors asked for more specifics about our information security and the protocols we have in place to safeguard our sensitive data. Naturally, those questions were directed toward the IT team (and were phrased in ISO 27001 terminology), which was initially challenging because we had limited knowledge of that particular standard.
How to Achieve ISO 27001: Everything You Need to Know to Pass the Audit
Welcome to our guide on ISO 27001 compliance! We’ll cover everything you need to know about ISO 27001, including its clauses, the preparation & audit processes, costs, and best practices. Let’s get started!
TrustCloud Releases World's First Free Security Questionnaire Tool and Compliance Sharing Portal for Startups
Building trust with vendor management
If you’re working towards a stronger security posture to become an organization that’s worthy of customer trust, your vendors are going to play an increasingly important role. In this article, we’ll give you an overview of vendor management and walk through what a robust vendor management process looks like.