Mastering Compliance in M365 Cloud Office Environments
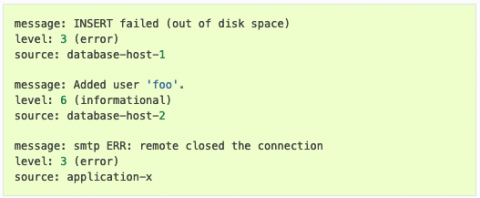
With the explosive growth of Microsoft 365, many companies are suddenly experiencing content sprawl at an unprecedented rate. What is content sprawl? It’s when your employees create unstructured content (files, chats, video) in the course of their workday, which then gets stored in multiple repositories, like SharePoint and OneDrive. Accelerate that in the context of a remote workforce, and you suddenly have content sprawling all over the place.