Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
What is ISO 31000? An Effective Risk Management Strategy
The Top 7 Cyberattacks on U.S. Government
In a world where ones and zeros are the new battleground, these threats, cyberattacks have become a significant threat to governments worldwide. The United States, with its vast array of government agencies and critical infrastructure, is no exception. Cybersecurity threats that impact the public sector range from state-sponsored attacks to financially motivated hacking groups. In this blog post, we’ll delve into the top 7 cyberattacks on the U.S.
3 Tangible Benefits of an A Rating
Security ratings are a standard in cybersecurity. Many organizations rely on them to manage their security programs and they create ROI for the organization. Despite the potential benefits, it can be challenging for organizations who are evaluating different security ratings options to determine the value they will get from them. When making investment decisions, it’s essential to know where the investment will take you and quantify that benefit.
Overcoming Cybersecurity Headwinds Part 1: Start With a Unified Approach
Cyber Risk Exposure: How to Act When You Can't Measure Risk
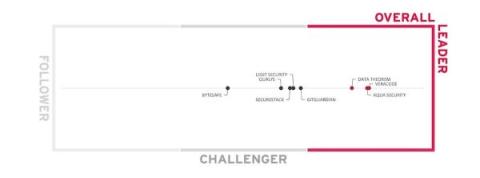
Why Reduce Software Supply Chain Risks with Intelligent Software Security
There’s a growing array of risks lurking within the supply chain of the digital solutions we increasingly depend upon. Leaving gaps in your software supply chain security (SSCS) could spell disaster for your organization. Let’s explore how new analysis defines an end-to-end solution and why Veracode was ranked as an Overall Leader, Product Leader, Innovation Leader, and Market Leader in the Software Supply Chain Security Leadership Compass 2023 by KuppingerCole Analysts AG.
Using a Standardized Approach for Measuring Cybersecurity in Government
Last week at the annual Billington CyberSecurity Summit in Washington, DC, officials from government agencies gathered with industry leaders to discuss cyber threats, as well as geopolitics and issues of national security. One of the highlights was a fireside chat on Friday with Anne Neuberger, deputy national security adviser for cyber and emerging technology.