Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
How to conduct a Privileged Access Management risk assessment
In today's business landscape, organizations rely heavily on digital systems, applications, and webpages for their daily operations. However, with the increasing use of technology comes growing risks of unauthorized access to sensitive information and data.
Template: Everything you Need to Craft a Supplier Risk Management Plan
Third-party vendors are a vital part of your business ecosystem. But if you’re not careful, these companies can introduce cyber risk. The SolarWinds supply chain hack is a notable example of the jeopardy that even the most trusted partnerships can yield. But with so many moving parts, creating a supplier risk management plan – and executing on it – can be a challenging and arduous task. According to Gartner, 60% of organizations work with more than 1,000 third-party vendors.
Unveiling the Future of AI in Cybersecurity
Welcome to our latest podcast episode, where we delve into the fascinating realm of AI in cybersecurity. Phil Agcaoili, the esteemed entrepreneur, and former CISO professional, joins us in this fascinating discussion. Alongside our hosts, Max Aulakh and Joel Yonts, we unravel the profound impact of artificial intelligence on cybersecurity, compliance, and the workforce.
How to Secure Your Expanding (and Hidden) Cybersecurity Ecosystem
Your organization’s cybersecurity ecosystem is complex. It covers a wide range of internal digital assets but also extends beyond the network perimeter to other entities, such as vendors, suppliers, and cloud service providers—making you increasingly vulnerable to cyber risk. To secure this ecosystem, you need both an outside-in and inside-out perspective of vulnerabilities and risks.
SecurityScorecard's Partnership with the TSA
As part of our continued commitment to making the world a safer place, SecurityScorecard recently partnered with the Transportation Security Administration (TSA). This partnership will enable the agency to more accurately monitor and assess the cyber health of the nation’s pipeline, rail, and aviation transportation systems.
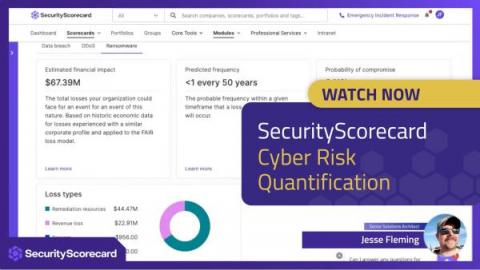
Translate Cyber Risk into Dollars With SecurityScorecard
Cyber risk is not just a security issue, it’s also a business issue. When security leaders and their businesses don’t see eye to eye, resources get misallocated, expectations aren’t met, and businesses are left unprepared to face threats. SecurityScorecard launched its Cyber Risk Quantification product in April 2022, allowing customers to quantify the financial impact of cyber risk and help facilitate collaboration and communication among business stakeholders.
Cybersecurity Risks in Hybrid Working Environments
Properly Explaining Risk Appetite to the C-Suite
In the first part of this series, we looked at some common issues when a Chief Information Security Officer (CISO) is communicating with the Board. At the heart of many of these issues is how the CISO and upper management view security. As one CISO recently told me, "It's a catch-22 situation: If the business leaders don't consider this to be a business problem, they are unlikely to listen to people they don't consider to be business leaders telling them it is.".