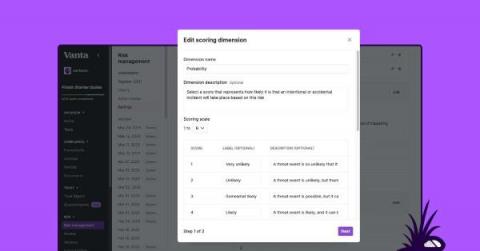
Fighting Together: TSA, Critical Infrastructure, and Cyber Risk Management
Following the ransomware attack on a US pipeline company in May of 2021, the Transportation Security Administration (TSA) issued a series of security directives to enhance the cybersecurity posture of US transportation systems to mitigate cyber threats.