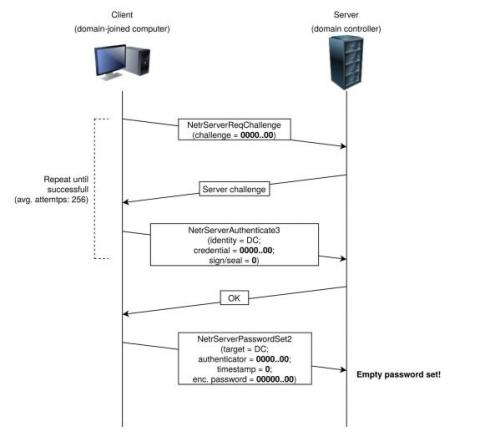
NSA list: what you need to know about the top vulnerabilities currently targeted by Chinese hackers Part 1
This week NSA published a list of the top 25 vulnerabilities that Chinese hackers are actively exploiting, and unsurprisingly the list included some of the most prominent CVEs that we’ve covered in our previous risk based vulnerability management blogs.