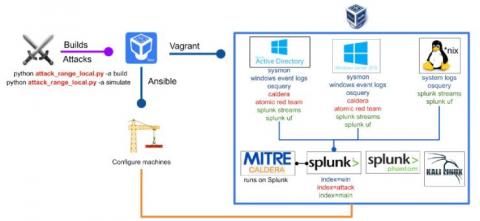
Zerologon: Tripwire Industrial Visibility Threat Definition Update Released
Today, we released a Threat Definition Update bundle for our Tripwire Industrial Visibility solution to aid in the detection of Zerologon. Otherwise known as CVE-2020-1472, Zerologon made news in the summer of 2020 when it received a CVSSv3 score of 10—the most critical rating of severity. Zerologon is a vulnerability that affects the cryptographic authentication mechanism used by the Microsoft Windows Netlogon Remote Protocol (MS-NRPC), a core authentication component of Active Directory.