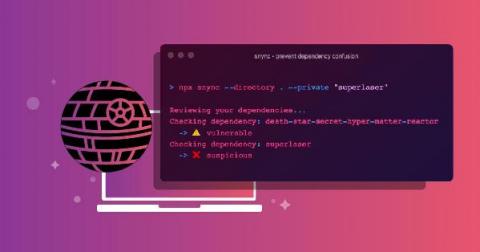
Apple's Vulnerability
Apple has issued an emergency software update after a cyber-surveillance company created invasive spyware that could infect any iPhone, iPad, Apple Watch, or Mac Computer. Toronto-based internet watchdog security group Citizen Lab said that NSO, the surveillance company which is an Israeli spyware company, developed the tool with a technique that could easily exploit Apple software.